Mandatory MFA for Admins and more (Entra, Intune, Azure)
As cyberattacks grow more frequent, protecting your infrastructure more important than ever. A key part is the enforcement of mandatory multifactor authentication (MFA) for all Azure sign-ins. MFA adds an essential layer of protection to your data, blocking over 99% of account compromise attempts.
Enforcement phase
Starting in the second half of 2024, Microsoft will roll out MFA requirements for all Azure sign-ins. The enforcement will happen in two phases:
Phase Description
- Phase 1: Enforcement starts for multiple web portals in the second half of 2024 (October 15, 2024).
- Phase 2: Delayed enforcement for most automation tools (e.g., PowerShell, CLI) starting early 2025 (Date TBD).
Enforcement Matrix
With the term "all Azure sign-ins" the following areas are currently targeted:
| App | User | Admin-User | Guest-User |
|---|---|---|---|
| Microsoft Entra admin center Link | (Yes) | Yes | (Yes) |
| Microsoft.Graph PowerShell Module | Yes delayed (Phase 2) | Yes delayed (Phase 2) | Yes delayed (Phase 2) |
| Microsoft Azure Link | (Yes) | Yes | (Yes) |
| Az PowerShell Module | Yes delayed (Phase 2) | Yes delayed (Phase 2) | Yes delayed (Phase 2) |
| Microsoft Intune admin center Link | Yes (AVD) | Yes | (Yes) |
| M365 Admin Center Link | No | No | No |
| Exchange Admin Center Link | No | No | No |
| Microsoft.Graph.Entra PowerShell Module 1 | Yes delayed (Phase 2) | Yes delayed (Phase 2) | Yes delayed (Phase 2) |
| Azure mobile app | Yes delayed (Phase 2) | Yes delayed (Phase 2) | Yes delayed (Phase 2) |
Verification (Impact)
You can verify which user accounts are signing in to admin portals without MFA enabled. There are different tools available from which I have picked two to show you some examples:
- Option 1: Analyze Sign-In Logs over PowerShell (Simple scenario)
- Option 2: Report for User registration details ('Entra ID Premium' needed)
- Option 3: MfaReport with MSIdentityTools (Complex scenario)
- Option 4: Multifactor Authentication Gaps ('Entra ID Premium' & 'Log Analytics workspace' needed)
Option 1 - Analyze Sign-In Logs with Graph
For a rather simple infrastructure, you can use Option 2 or the following script snippet (if no 'Entra ID Premium' license is available):
1 2 3 4 5 6 7 8 9 10 11 12 | |
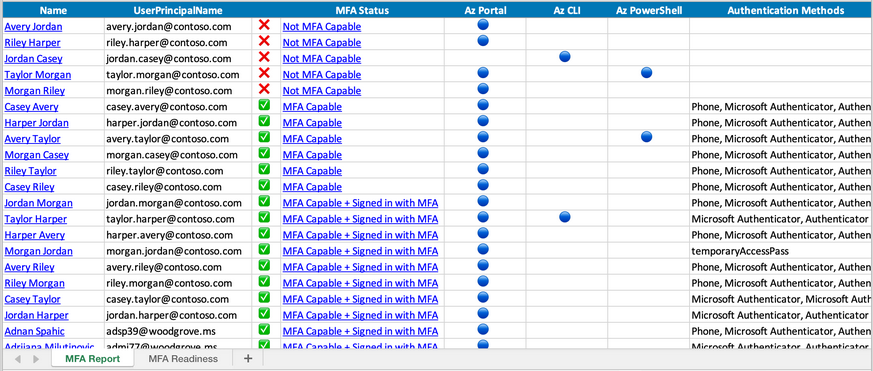
Option 3 - MfaReport with MSIdentityTools
For a more detailed report and probably complex infrastructure, you can use the MfaReport or Option 4 (repeatedly).
Exports the list of users that have signed into the Azure portal, Azure CLI, or Azure PowerShell over the last 30 days by querying the sign-in logs. In Microsoft Entra ID Free tenants, sign-in log retention is limited to seven days.
1 2 3 | |
Opt-out (Postpone)
There's no way to fully opt out of the MFA enforcement, but you can postpone it. Global Administrators can delay the MFA enforcement start date to March 15, 2025, for their tenants. This postponement is designed for organizations with complex environments or technical barriers.
PS: Keep in mind, postponing adds security risks, as accounts without MFA remain vulnerable to attacks. Limit access over Conditional Access as an alternative.
Summary
Microsoft’s mandatory MFA for Azure is a critical security enhancement designed to protect your data from growing cyber threats.
I would state that this change presents some challenges, as any security enhancement does, requiring resources to be allocated. However, it also is a learning opportunity for IT admins to adopt more advanced methods like FIDO2 (for example in the case of break-glass/emergency accounts), which can improve their knowledge. Hopefully, this shift will also encourage some to remove trusted location exclusions.
With Phase 2, we will see the overdue migration of user-based service accounts to workload identities (app registration), mostly used in automation processes. Wishing you all a productive day ahead!
References:
- MC862873 - Take action: Enable multifactor authentication for your tenant before October 15, 2024
- Generally Available: Enable multifactor authentication for your tenant by 15 October 2024
- Planning for mandatory multifactor authentication for Azure and other admin portals
- Announcing mandatory multi-factor authentication for Azure sign-in
- MSIdentityTools
