Managed Conditional Access Policy
Microsoft Entra ID provides Managed Conditional Access Policies to help organizations enforce security best practices. These pre-configured policies simplify implementation while ensuring key protections like multifactor authentication (MFA) and blocking legacy authentication. They will be extended in February 2025 and after a 45 trial period automatically activated:
- Block device code flow [NEW]
- Block legacy authentication [NEW]
Overview
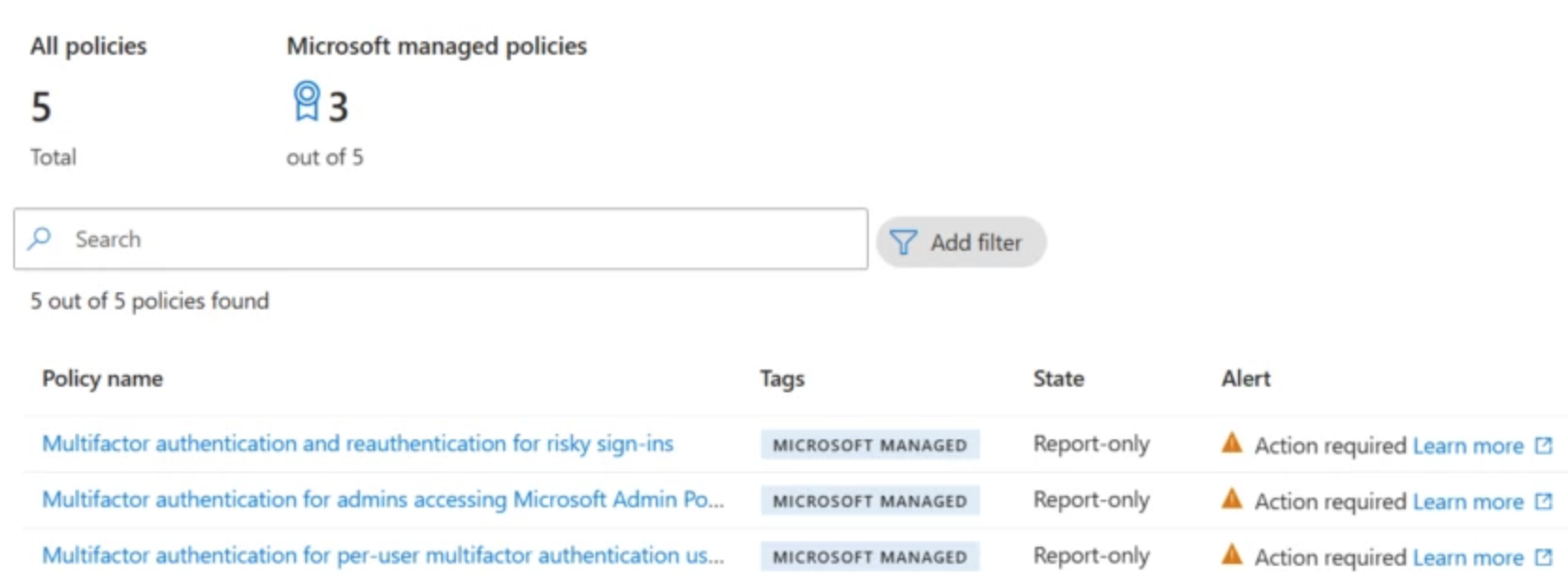
The table below summarizes the currently available managed policies:
| Policy Name | Target Audience | Description | Rollout Status |
|---|---|---|---|
| Multifactor authentication for admins accessing Microsoft Admin Portals | Admins1 (or VDI-User3) | Enforces MFA when accessing Microsoft Admin Portals | Completed |
| Multifactor authentication for per-user multifactor authentication users | Users2 with Legacy MFA Settings | Applies MFA to users with per-user MFA configured | Completed |
| Multifactor authentication and reauthentication for risky sign-ins | Users2 with Risk Detections | Requires MFA or reauthentication for sign-ins flagged as risky | Rollout |
| N/A (Block device code flow) | Users2 which are using Device Code Flow | Manages cross-device authentication scenarios | Planned (March 2025) |
| N/A (Block legacy authentication) | Users2 which are using Basic Authentication | Blocks legacy authentication on legacy protocols (POP, SMTP, IMAP, MAPI) to improve security | Planned (March 2025) |
Risk of confusion
There can be confusion between Security Defaults and Microsoft-managed conditional access because both are designed to secure Microsoft 365 environments, but they operate differently:
- Security Defaults are part of the Entra Free tier, offering basic protection (small businesses).
- Microsoft-managed conditional access, available in Entra P1 and P2, offers more customizable and granular security controls, allowing businesses to enforce specific policies based on user behavior and risk (medium to enterprise businesses).
Managed policy are always marked with a tag "Microsoft Managed" (Link to portal):
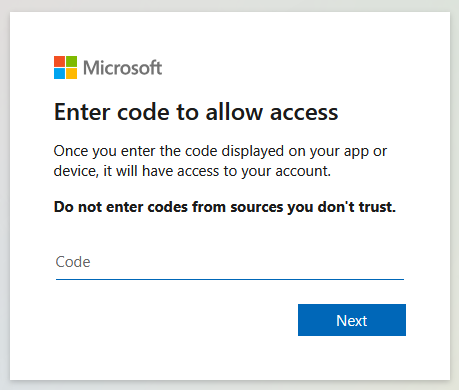
Device Code (Example 1)
Device code authentication (OAuth 2.0 device authorization) is a secure method used for authenticating devices that do not have a web browser or limited input capabilities. It allows users to authenticate by entering a code on another device with a browser, simplifying login processes while maintaining security through OAuth 2.0 protocols.
However, it is:
- Rarely used in practice, aside from targeted phishing attacks
- Occasionally misused as a workaround for certain applications
1 2 3 4 | |
Alternative: Enable Device Code only where needed (reduce risk)
Basic Auth (Example 2)
Basic Authentication is commonly used in legacy protocols like IMAP, SMTP, and others, where credentials (username and password) are sent with each request. While simple, it's insecure, vulnerable to attacks like man-in-the-middle (MITM).
In this regard, it is:
- Occasionally used for legacy systems that have not been updated to support more secure authentication methods (not recommended for production environments anymore)
- Set to be deprecated: Exchange Online will remove support for Basic Auth with SMTP AUTH in September 2025.
1 2 3 4 5 6 7 | |
Alternative: Use SMTP or IMAP with Modern Auth (OAuth2)4
Summary
The new changes to Microsoft Entra ID’s Managed Conditional Access Policies, including the blocking of device code flow and legacy authentication, are part of the Secure Future Initiative (SFI). These updates enhance security and simplify enforcement. Managed policies offer organizations customizable security controls, ensuring better protection against risks.
I would recommend reviewing your Sign-In logs to align policies with current needs and prepare for future deactivation. Additionally, discuss with third parties and set deadlines for phasing out legacy protocols.
References:
- New Microsoft-managed policies to raise your identity security posture
- Microsoft-managed policies
- Microsoft identity platform and the OAuth 2.0 device authorization grant flow
- Deprecation of Basic authentication in Exchange Online
- Exchange Online to retire Basic auth for Client Submission (SMTP AUTH)
- Authenticate an IMAP, POP or SMTP connection using OAuth
